ENG | MikroTik NAT Example: Internal & External SSH Access
Configuring DNAT and SNAT rules on MikroTik for seamless internal and external access to a local server (port forwarding on consumer routers)
This article is basically a recap of Claude.AI Sonnet 3.5 conversation with added scheme.
Problem
You need to redirect incoming connections to pavelp.cz:2222 to your internal server (192.168.68.10:22).
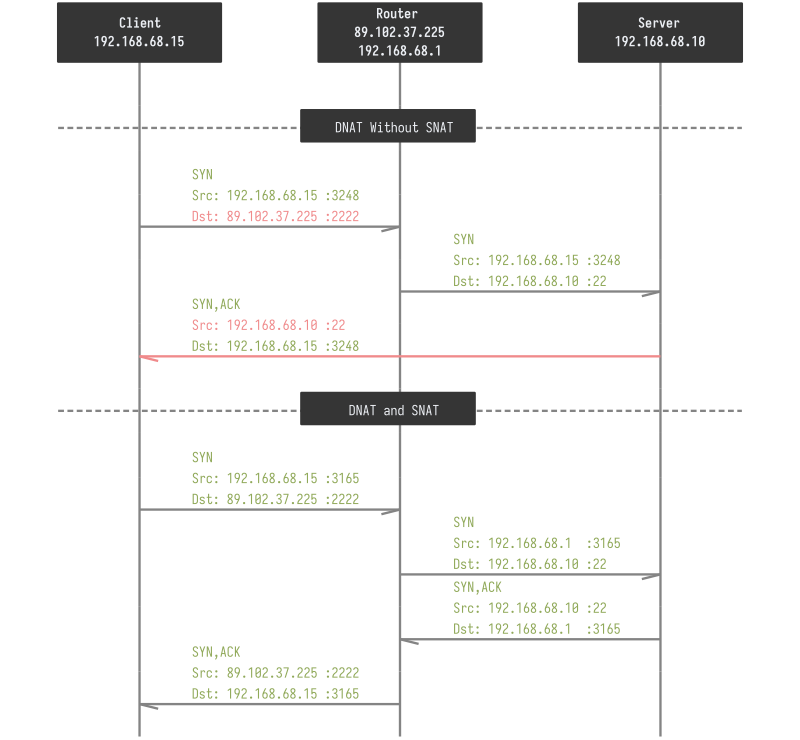
While external access works, internal access fails due to the lack of NAT hairpinning (also known as NAT reflection).
Concept
This solution involves two types of NAT:
- Destination NAT (DNAT): Modifies the destination of incoming packets.
- Source NAT (SNAT): Modifies the source of outgoing packets.
Solution
- DNAT rule for external traffic:
1
/ip firewall nat add chain=dstnat action=dst-nat protocol=tcp dst-port=2222 in-interface=wan to-addresses=192.168.68.10 to-ports=22
This redirects incoming WAN traffic on port 2222 to your internal server.
- DNAT rule for internal traffic:
1
/ip firewall nat add chain=dstnat action=dst-nat protocol=tcp dst-port=2222 dst-address=<wan_interface_name> to-addresses=192.168.68.10 to-ports=22
This handles internal requests to your public IP (or interface) on port 2222.
- SNAT rule for return traffic:
1
/ip firewall nat add chain=srcnat action=masquerade protocol=tcp src-address=192.168.68.0/24 dst-address=192.168.68.10 dst-port=22
This ensures proper routing of return traffic for internal clients.
Why it works
- External access: The first DNAT rule redirects incoming connections from the WAN to your internal server.
- Internal access: The second DNAT rule catches internal requests to your public IP/interface and redirects them to the internal server.
- The SNAT (masquerade) rule changes the source of internal packets to the router’s IP, allowing the server to reply correctly. Without this rule, server replies directly to client (it’s on the same network), but with it’s own IP address and port that differs from request.
This configuration enables both external and internal clients to access the service at pavelp.cz:2222, with all traffic properly redirected to 192.168.68.10:22. It works with a dynamic public IP by using the WAN interface name instead of a specific IP address.
Remember to adjust network addresses if your local subnet differs, and ensure these rules are placed correctly in your NAT table, typically with DNAT rules before general masquerade rules.
This setup provides a robust solution for accessing your internal server from both inside and outside your network, handling the complexities of NAT traversal and maintaining functionality even with a dynamic public IP address.
Addendum
All at once (first line is default)
1
2
3
4
5
/ip firewall nat
# add action=masquerade chain=srcnat comment="defconf: masquerade" ipsec-policy=out,none out-interface-list=WAN
add action=dst-nat chain=dstnat comment="SSH from outside" dst-port=2222 in-interface-list=WAN protocol=tcp to-addresses=192.168.68.10 to-ports=22
add action=dst-nat chain=dstnat comment="SSH from inside" dst-port=2222 in-interface-list=LAN protocol=tcp to-addresses=192.168.68.10 to-ports=22
add action=masquerade chain=srcnat comment="SSH from inside (snat)" dst-address=192.168.68.10 dst-port=22 protocol=tcp src-address=192.168.68.0/24